When accessing some of the Microsoft Graph API endpoints, you can get away with leveraging the well known Client ID reserved for PowerShell: “1950a258-227b-4e31-a9cf-717495945fc2”. Of course luck would have it, the few items I wanted to access (Microsoft Graph Reporting API and Office 365 Management Activity API) are not granted to the PowerShell Client ID.
Most people would just go into the Azure Portal and manually create an Azure Application Registration using one of the thousands how-to guides (example: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-integrating-applications or https://blogs.technet.microsoft.com/dawiese/2017/04/15/get-office365-usage-reports-from-the-microsoft-graph-using-windows-powershell/).
I, on the other hand… If using PowerShell to access Graph, why not use Graph to also create the Azure Application Registration?
Manage-AzureAppRegistration can be found on the TechNet Gallery:
Script Download: Manage-AzureAppRegistration.ps1
https://gallery.technet.microsoft.com/Manage-AzureAppRegistration-0f3256c6
The script has a prerequisite of having at least one of the following PowerShell Modules installed to load the Active Directory Authentication Library (ADAL) DLL:
- Azure Service Management PowerShell Module
- Azure Active Directory PowerShell Module
- Azure Resource Manager PowerShell Module
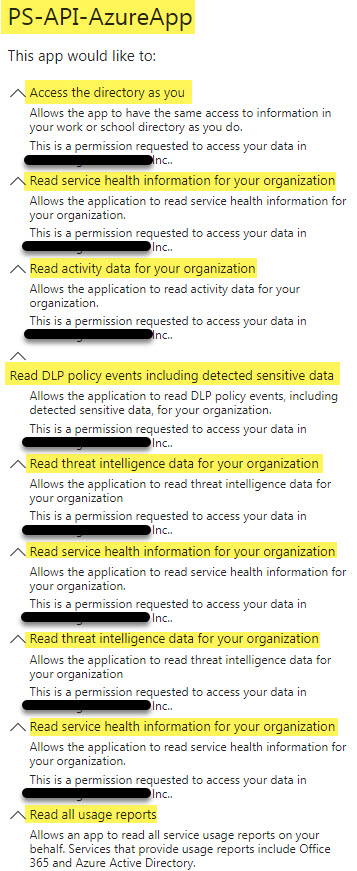
By default running .\Manage-AzureAppRegistration.ps1 will prompt for an Azure Tenant AD Domain Name (domain.onmicrosoft.com), prompt for tenant Administrative credentials before creating the Azure Application Registration with a default name of “PowerShell-API-AzureApp” (unless -appname is used to override). The script will create the Application, Service Principal and grant Oauth2 Permissions to the user running the script. If any of the Application/Service Principal/Oauth2Permissions exist, each will be checked, created or updated as required. Missing Permissions or Access are only added and existing settings in addition are not removed.
Manage-AzureAppRegistration defaults with the following Required Resource Access:
- Windows Azure Active Directory: Same access to information in the directory as the signed-in user
- Microsoft Graph: Read all service usage reports on behalf of the signed-in user
- Office 365 Management APIs: All items
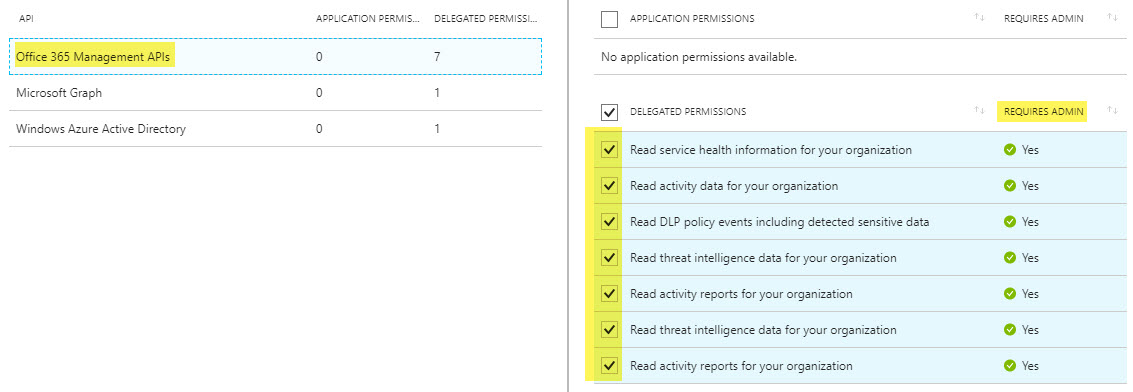
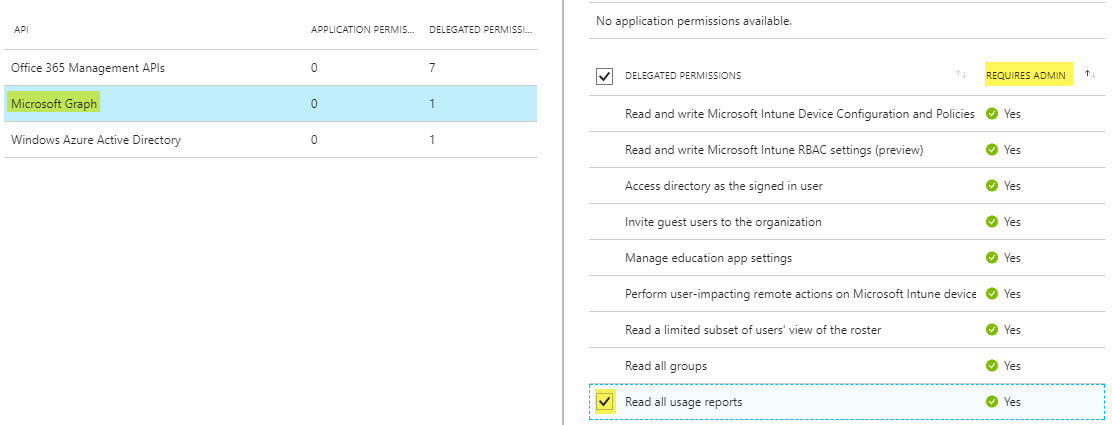
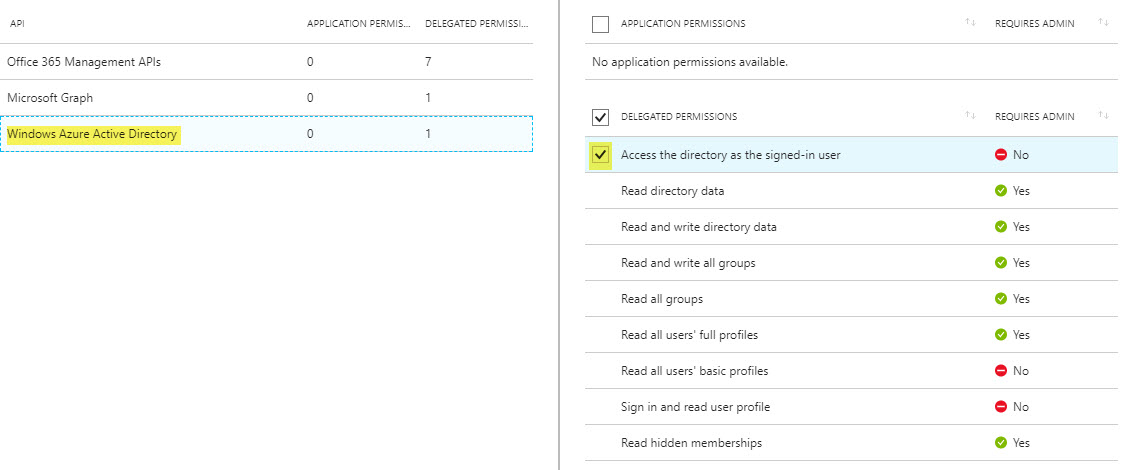
At this point, with the above access I’m able to use PowerShell to access the Graph items that didn’t work with the native PowerShell Client ID. I’ll be blogging about those in the near future. Feel free to modify Manage-AzureAppRegistration, to tweak the Required Resource Access to fit your needs.
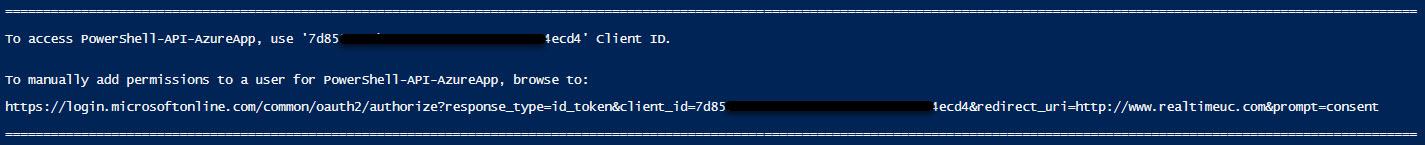
The script will output the Client ID for the registered Application, also the Manual Consent URL if you would like other Administrative accounts to leverage the Application.
- Fun fact #1: Starting with AzureAD PowerShell Module: v2.0.0.98; The Microsoft.IdentityModel.Clients.ActiveDirectory.dll also requires Microsoft.IdentityModel.Clients.ActiveDirectory.Platform.dll and UserCredential changed to UserPasswordCredential.
- Fun fact #2: Microsoft Internal Service Principals can have different display names across tenants and some of these Service Principals might not even be listed in a specific tenant, unless using a filter with the hard coded APPID.
Script Download: Manage-AzureAppRegistration.ps1 https://gallery.technet.microsoft.com/Manage-AzureAppRegistration-0f3256c6
