While writing the Manage-AzureAppRegistration script ( http://realtimeuc.com/2017/12/manage-azureappregistration/), I found some interesting problems setting Oauth2Permissions. My original code would lookup the Service Principal for an API to assist with determining the ID for the specific role I was adding. The problem quickly became apparent that not all Tenants had the same list of Microsoft Service Principals and even if they did, the Display Name could be different.
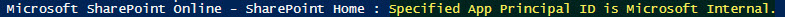
Trying to be clever, I attempted to use Graph to reconstruct the Office 365 Management APIs Service Principal and was nicely greeted with “Specified App Principal ID is Microsoft Internal” when doing a post to the Graph Azure Service Principal endpoint. After hitting that wall, I just tweaked my code to set the permissions using the Known Resource App ID of the Microsoft API. This worked because Graph is aware of the Microsoft API Service Principals even if not listed on the specific Tenant. Same reason you can select any of these APIs in the Azure Portal when modifying an Application’s permissions.
Armed with the information that I could take all the Service Principals in a Tenant and do a simple Graph post, I could determine out of the 100+ items which ones were known to Microsoft and those not. Fun fact, using the known PowerShell Client ID “1950a258-227b-4e31-a9cf-717495945fc2” for the Graph Token, does not expose the “Microsoft Internal” post response. You will need to register an Azure application and use that Client ID (see Manage-AzureAppRegistration URL above for details).
PowerShell Client ID:
 New Azure Application Client ID:
New Azure Application Client ID:
Check-AzureServicePrincipals can be found on the TechNet Gallery:
Script Download: Check-AzureServicePrincipals.ps1
https://gallery.technet.microsoft.com/Check-AzureServicePrincipal-4618d512
The script has a prerequisite of having at least one of the following PowerShell Modules installed to load the Active Directory Authentication Library (ADAL) DLL:
- Azure Service Management PowerShell Module
- Azure Active Directory PowerShell Module
- Azure Resource Manager PowerShell Module
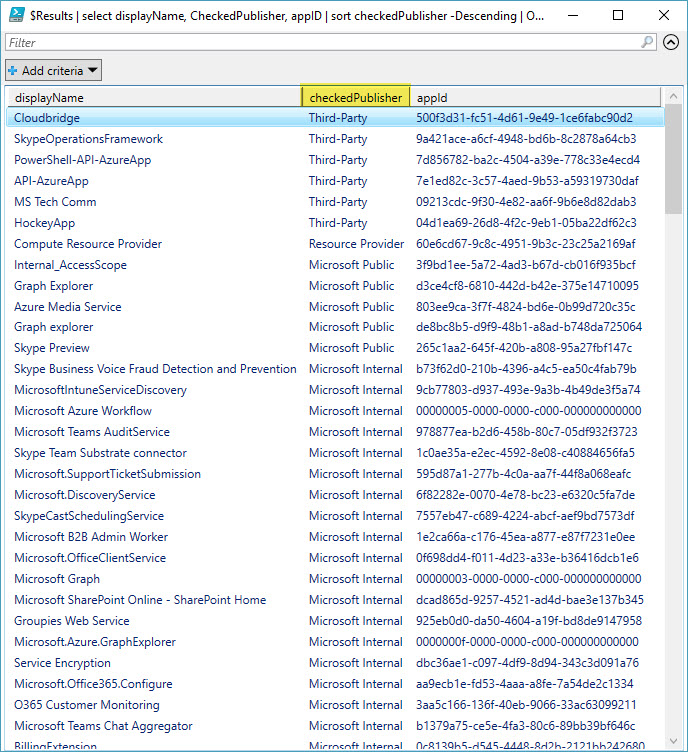
Check-AzureServicePrincipals will return an object with all the normal Service Principal properties plus an added item “checkedPublisher”. This property will have one of four labels:
- Microsoft Internal: Returned by Graph
- Microsoft Public: A check against the $KnownServicePrincipass array in the script
- Resource Provider: Publisher Name equal to “Microsoft Service”, these could still be non-Microsoft applications
- Third-Party: All items not tagged with the above
Example:
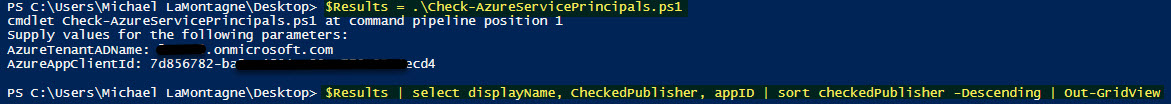
$Results = .\Check-AzureServicePrincipals.ps1
$Results | select displayName, CheckedPublisher, appID | sort checkedPublisher -Descending | Out-GridView
Script Download: Check-AzureServicePrincipals.ps1 https://gallery.technet.microsoft.com/Check-AzureServicePrincipal-4618d512
