What is 3DES and does the removal mean anything to your organization?
Just in time for the holidays, Microsoft announced a major update to Office 365: “We’re retiring 3DES in Office 365 beginning February 28, 2019."
Microsoft announced on April 18, 2019 an updated timeline for 3DES retirement: “Starting July 10, 2019, Office 365 Skype for Business will begin retiring 3DES”
-
September 2017: On an Office 365 Partner slide -
Starting March 2018, we will no longer support versions of Transport Layer Security (TLS) < 1.2. Users and apps connecting to Microsoft Online Services using TLS 1.0 or 1.1, need to migrate to TLS 1.2+. More information: TLS 1.2 Support at Microsoft: https://cloudblogs.microsoft.com/microsoftsecure/2017/06/20/tls-1-2-support-at-microsoft/
-
December 2017: Mandatory use of TLS 1.2 in Office 365 -
Added Mandatory use of TLS 1.2 in Office 365 - action required by March 1, 2018
https://blogs.technet.microsoft.com/skywriter/2017/12/27/office-365-planned-service-changes-december-2017-updates/ -
February 2018: An Update on Office 365 Requiring TLS 1.2 -
We would like to bring to your attention an update on Office 365’s plans to enforce TLS 1.2, which has now been communicated in this KB article (KB4057306). The end of support for TLS 1.0 and TLS 1.1 has been moved from March 1st, 2018, to October 31st, 2018 to allow for more time to prepare.
https://blogs.technet.microsoft.com/exchange/2018/02/09/an-update-on-office-365-requiring-tls-1-2/ -
September 2018: No Support TLS 1.0/1.1 vs. Mandatory TLS 1.2 -
As of October 31, 2018, Office 365 will no longer support TLS 1.0 and 1.1. This means that Microsoft will not fix new issues that are found in clients, devices, or services that connect to Office 365 by using TLS 1.0 and 1.1.
https://support.microsoft.com/en-gb/help/4057306/preparing-for-tls-1-2-in-office-365 -
October 2018: Microsoft Teams Direct Routing (sip.pstnhub.microsoft.com) removal of TLS 1.0/1.1 and cipher change -
Welcome to the cloud! Overnight Microsoft’s Teams Direct Routing SBCs moved to only supporting the following Cipher Suites and TLS 1.2+:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
TLS handshake now requires supported elliptic curves: P-384 (secp384r1) (384 bits) / P-256 (prime256v1) (256 bits)
-
December 2018: Plan to move to TLS 1.2+ and 3DES removal from Office 365 -
As previously communicated (MC124104 in October 2017, MC126199 in December 2017 and MC128929 in February 2018), we are planning to move all of our online services to Transport Layer Security (TLS) 1.2+ to provide best-in-class encryption, and to ensure our service is more secure by default.
As part of this plan, we’ll be retiring 3DES beginning February 28, 2019.
https://admin.microsoft.com/AdminPortal/home?switchtomodern=true#/MessageCenter?id=MC171089 -
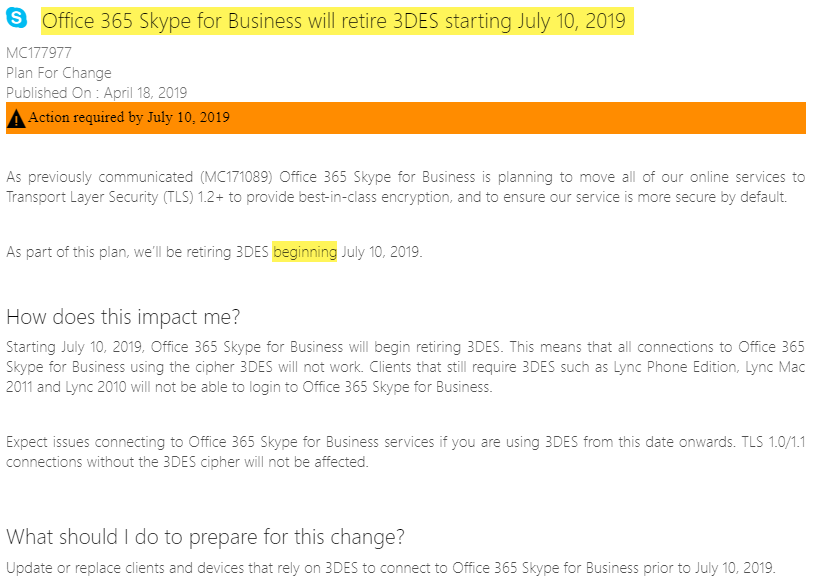
April 2019: Office 365 Skype for Business will retire 3DES starting July 10, 2019 -
As previously communicated (MC171089) Office 365 Skype for Business is planning to move all of our online services to Transport Layer Security (TLS) 1.2+ to provide best-in-class encryption, and to ensure our service is more secure by default. As part of this plan, we’ll be retiring 3DES beginning July 10, 2019.
https://admin.microsoft.com/AdminPortal/home?switchtomodern=true#/MessageCenter?id=MC177977 -
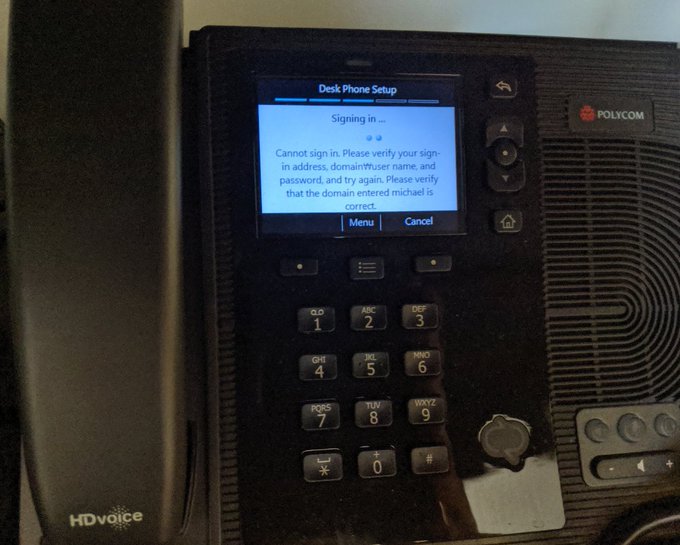
October 2019: Lync Phone Edition no longer able to sign into Office 365 -
3.5 months after the July 10, 2019 deadline for 2DES: LPE no longer able to sign into Office 365!
-
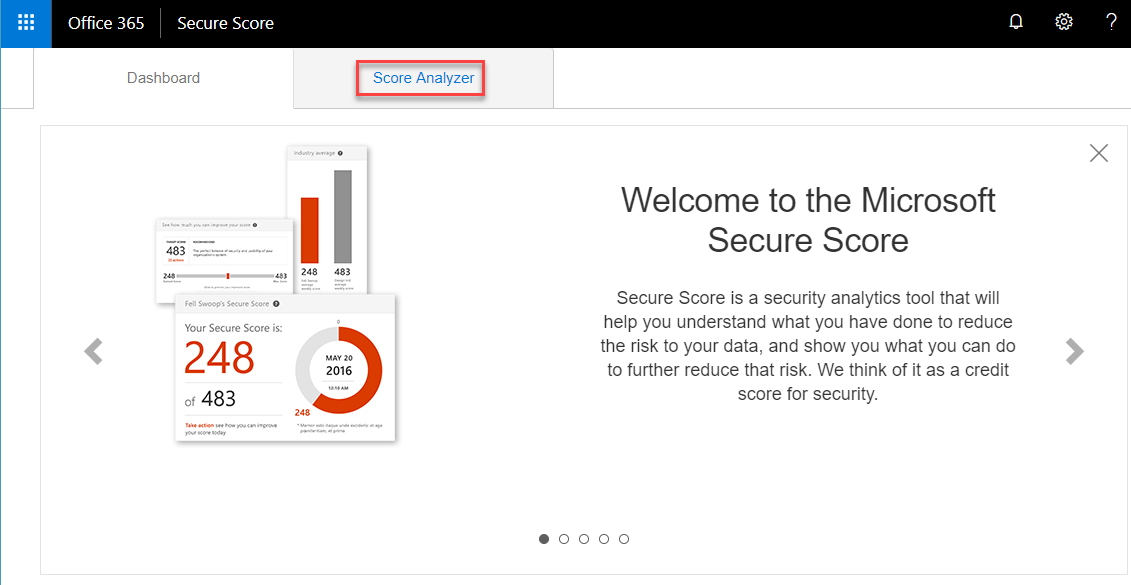
Sign into Microsoft’s Secure Score: https://securescore.office.com and click on ‘Score Analyzer’.
-
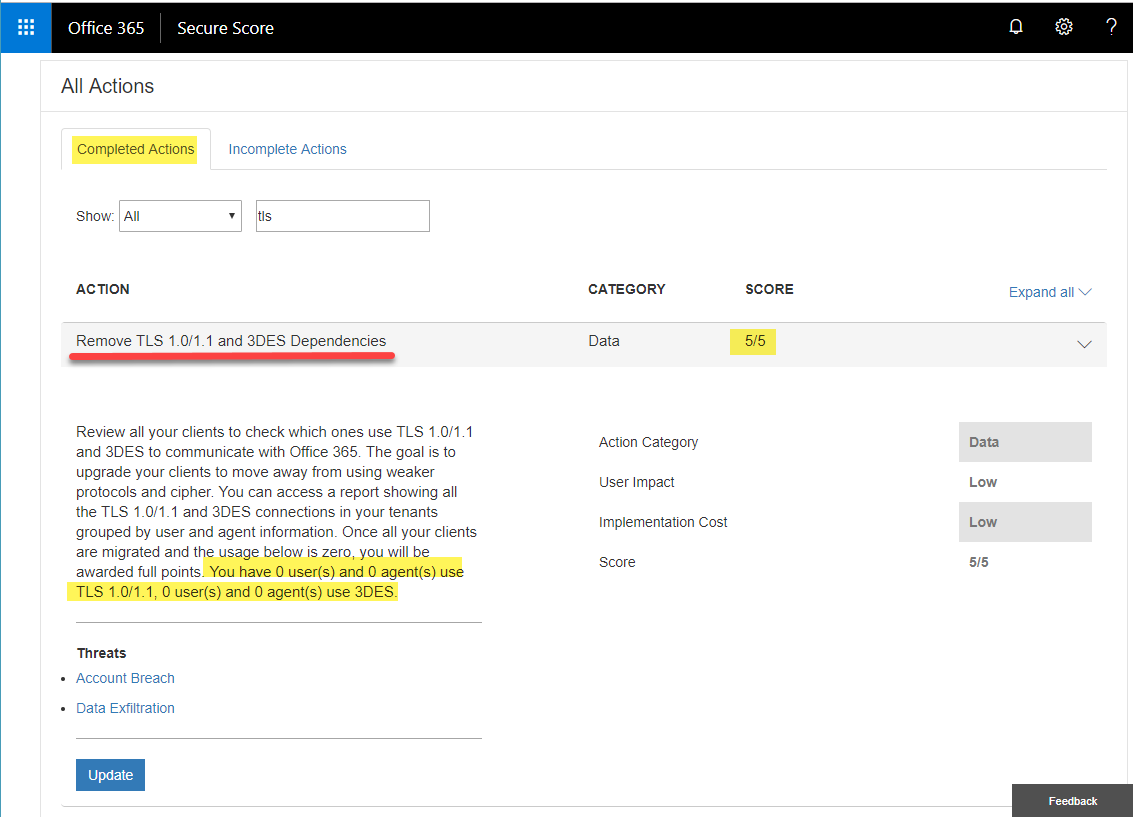
Scroll down to ‘All Actions’ and search under both ‘Completed Actions’ & ‘Incomplete Actions’ for ’tls’. Review the last sentence in the body of the Action, hopefully you have 0 users and 0 agents for both TLS 1.0/1.1 and 3DES.
No Impact:
Impact:
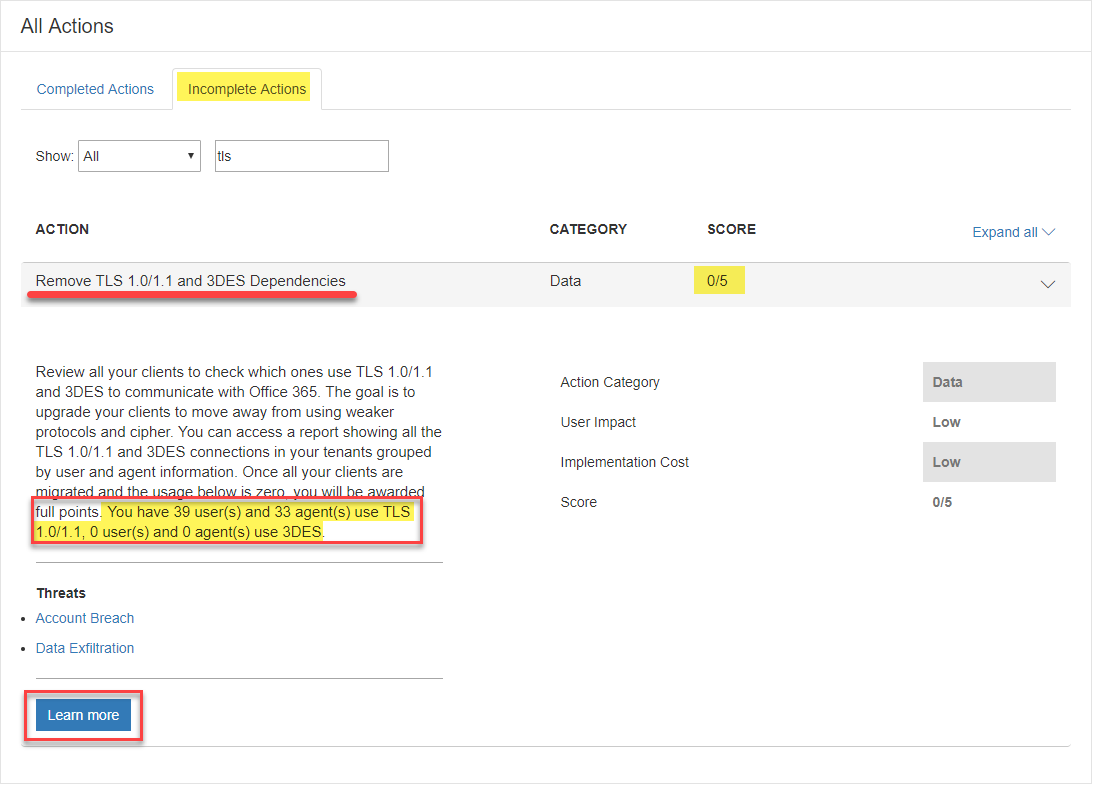
-
If you have Users or Agents that are listed as impacted, click on the ‘Learn More’, a flyout panel will appear and click ‘Launch Now’ ( TLS Deprecation Report).
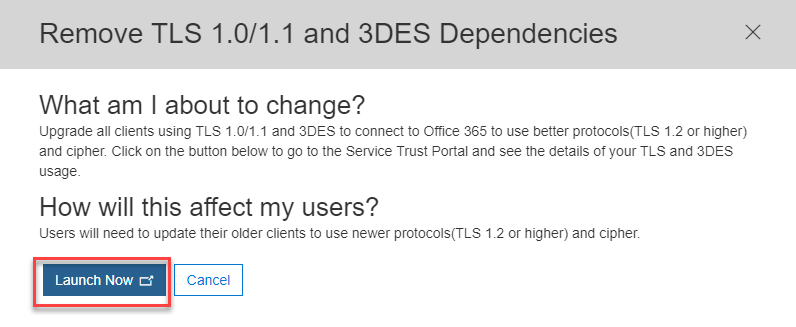
-
Sign into Microsoft’s Service Trust Portal, click ‘Download’ and save TLS-Deprecation-Report.csv.
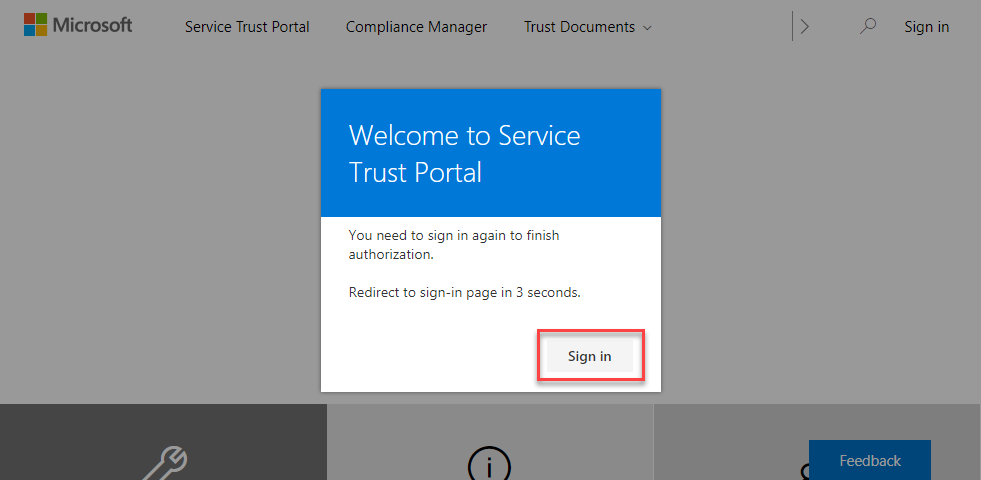
-
Review results, plan and address!
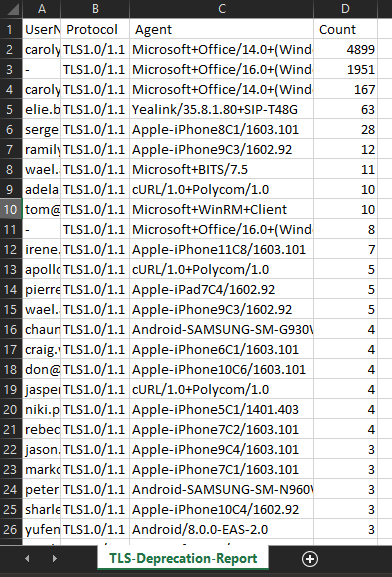
A sample list of items to watch for:
- Windows 7 or 2008R2 and earlier
- Android 4.3 and earlier
- Office 2007 and earlier
- Lync 2010 clients
- Lync Phone Edition
- Lync Mac 2010 & 2011
- Lync Room System (SRSv1)
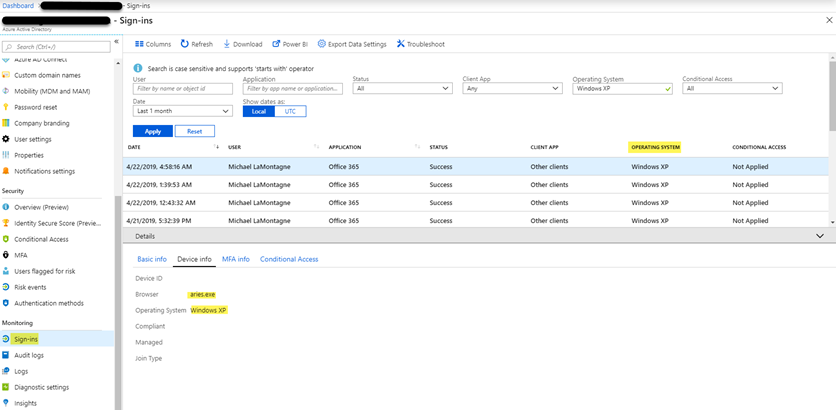
For organizations that have access to the Azure Active Directory Sign-ins monitoring, you can add the Operating System column and search for “Windows XP”. In the Device info you will see the Browser for Lync Phone Edition devices to be “aries.exe”.
- An excellent post about Lync Phone Edition TLS limitations by Trevor Miller: https://ucvnext.org/2016/03/lync-phone-edition-tls-limitations/
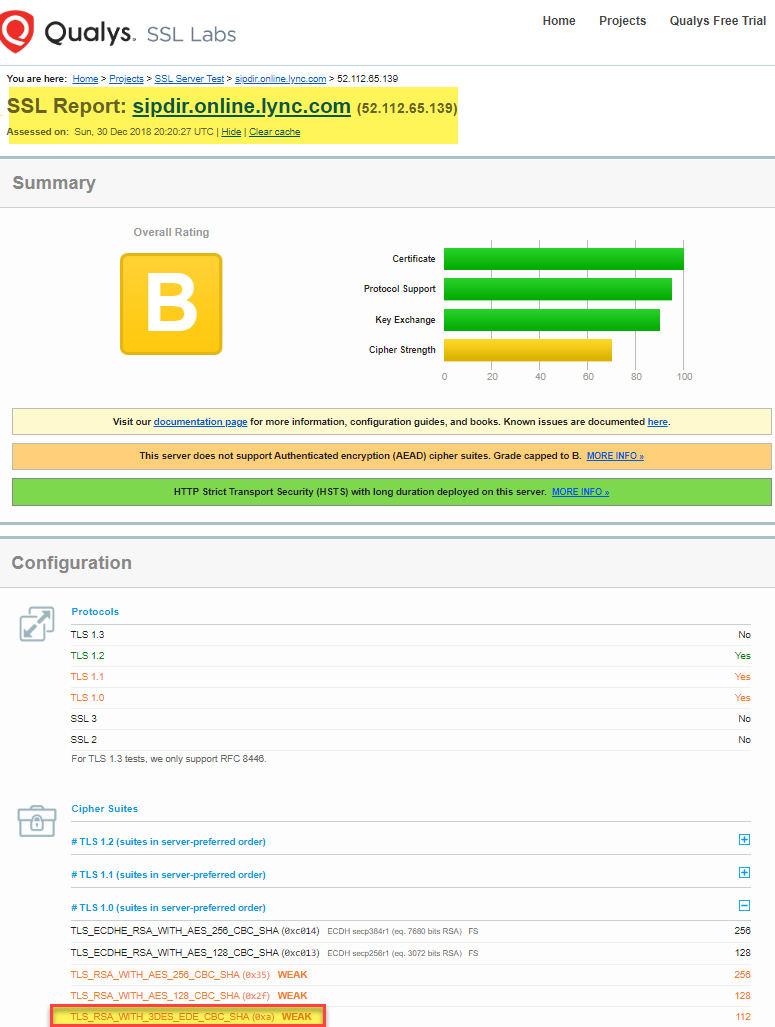
If you look at an
SSL Report for sipdir.online.lync.com, the only supported cipher that LPE supports is TLS_RSA_WITH_3DES_EDE_CBC_SHA. Once 3DES is removed, there will be no workaround for LPE to connect to Office 365 services.